The giant network on the Internet for web application security and performance, Cloudflare DNS Service was recently disrupted by a BGP hijacking incident. The loss has caused significant impact on its DNS resolver service, 1.1.1.1. This incident, which involved a combination of Border Gateway Protocol (BGP) hijacking and a route leak, affected 300 networks across 70 countries. Although the overall impact was described as “quite low,” some users in certain regions did not notice the issue.
Incident Details
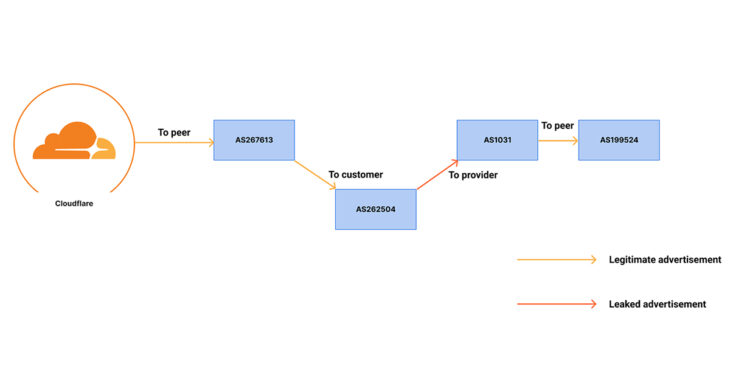
The disruption began at 18:51 UTC on June 27, when Eletronet S.A. (AS267613) mistakenly announced the 1.1.1.1/32 IP address to its peers and upstream providers. This incorrect announcement was accepted by multiple networks, including a Tier 1 provider, which treated it as a Remote Triggered Blackhole (RTBH) route. Since BGP routing favors the most specific route, AS267613’s announcement of 1.1.1.1/32 was preferred over Cloudflare’s 1.1.1.0/24, leading to incorrect traffic routing and causing the DNS resolver service to become unavailable for some users.
Just a minute later, at 18:52 UTC, Nova Rede de Telecomunicações Ltda (AS262504) accidentally leaked the 1.1.1.0/24 IP address upstream to AS1031, which propagated it further, affecting global routing. This leak compounded the hijacking problem, causing additional reachability and latency issues.
Remediation Efforts
Cloudflare identified the problems at around 20:00 UTC and took immediate steps to resolve the issues. The hijack was addressed roughly two hours later, and the route leak was resolved at 02:28 UTC. The company engaged with the networks involved and disabled peering sessions with problematic networks to mitigate the impact and prevent further propagation of incorrect routes.
Long-term Solutions
To prevent similar incidents in the future, Cloudflare has proposed several long-term solutions, including:
- Enhancing route leak detection systems by incorporating more data sources and integrating real-time data points.
- Promoting the adoption of Resource Public Key Infrastructure (RPKI) for Route Origin Validation (ROV).
- Encouraging the adoption of the Mutually Agreed Norms for Routing Security (MANRS) principles, which include rejecting invalid prefix lengths and implementing robust filtering mechanisms.
- Advocating for networks to reject IPv4 prefixes longer than /24 in the Default-Free Zone (DFZ).
- Supporting the deployment of ASPA objects (currently drafted by the IETF), which are used to validate the AS path in BGP announcements.
- Exploring the potential of implementing RFC9234 and Discard Origin Authorization (DOA).
While the incident caused disruptions, Cloudflare quick response and proposed long-term measures aim to enhance the resilience of its DNS services against future BGP hijacking and route leak incidents. By adopting these practices, Cloudflare seeks to improve the overall security and reliability of its network infrastructure.
Recent Articles:
New Ransomware Behind Indonesia’s Data Center Attack
Chinese Hackers Breach 20,000 FortiGate Systems Worldwide
Chinese Spy in Cuba: US Reaction