The online security of digital accounts and sensitive information has become more critical than ever. Cybercriminals have become increasingly adept at breaching systems and stealing data. They can crack 90% of passwords easily within an hour. That’s why making advanced authentication methods is very essential for businesses and individuals. Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) are two of the most effective tools in maximizing cybersecurity and preventing against most common cyber attacks especially Phishing Attacks which are widely increasing. This article will eloborates the differences between 2FA and MFA, their benefits, and why they are crucial for protecting your digital identity.
What is Authentication?
Authentication is the process of verifying your identity to access networks, accounts, or systems. Every time you enter a password to log into an account, you’re authenticating that you are the authentic (real owner) user. However, passwords alone have become less secure as cybercriminals have been developing sophisticated methods to crack them. Most people use weak, easily guessable passwords or reuse the same passwords across multiple accounts, and this increase the risks of being hacked, putting individuals & businesses in worst situation.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a secure security process that requires two forms of identification to verify a user’s identity while log-in. The first factor is your username and password, and the second is an additional method, such as a text message code, email verification, or biometric scan etc. For example, when you log into an account from a new device, you may receive a text message with a verification code that you must enter to complete the login.
Types of 2FA Methods
- SMS Codes: A code can be sent to your mobile phone number or via WhatsApp number.
- Email Verification: A code sent to your email address which you use for authentication methods.
- Physical Tokens: Devices like key fobs or USB keys are being used for 2FA.
- Biometrics: Fingerprint readers or iris scanners are also common types of 2FA.
- Mobile Apps: Apps like Authy, Google Authenticator or any authenticator app which is installed onto your phone, that generate one-time use codes.
What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) goes beyond than 2FA by requiring two or more additional authentication factors. The first factor is your username and password, and the subsequent factors are additional methods chosen from different categories. To understand the difference between 2FA and MFA you need to know the types of authentication factors, as below:
Four Types of Authentication Factors:
- Something you know: Password, PIN, or security question.
- Something you have: Physical token or virtual token such as a One-Time Password (OTP) or Time-Based One-Time Password (TOTP).
- Something you are: Biometric data such as Face ID or fingerprint.
- Somewhere you are: Apps and services only accessible to users within a specific geographic location.
While 2FA falls under the umbrella of MFA. The MFA is broader and more flexible, offering greater and extra online security by combining different types of authentication factors.
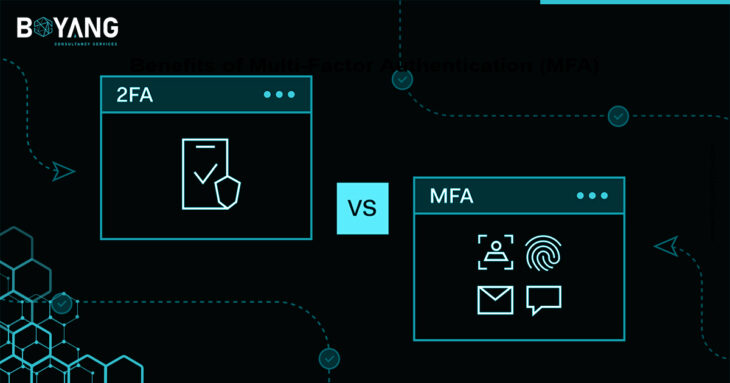
Differences Between 2FA and MFA
The main difference between Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) lies in the number of authentication methods required which makes them less or more secure, like:
- 2FA: Requires only two authentication factors, which can be from the same category (e.g., a password and a PIN).
- MFA: Requires at least two or more than two authentication factors from different categories (e.g., a password, a biometric scan, and a security token).
This means MFA is generally more secure than 2FA, as it makes it more difficult for cybercriminals to bypass multiple layers of security.
Is MFA More Secure Than 2FA?
Yes, the Multi-Factor Authentication (MFA) is more secure than 2FA because it uses multiple methods to verify a user’s identity. Both Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) are different types as compare to each other. This layered approach significantly reduces the likelihood of unauthorized access.
The Importance of 2FA and MFA
Both Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) are crucial for enhancing security in the following ways:
- Provides Extra Layers of Security: Without additional authentication, anyone with access to your password can access your accounts. 2FA and MFA add extra layers of protection, reducing the risk of unauthorized access.
- Protects Against Compromised Passwords: If a password is compromised, the additional authentication factor(s) can prevent cybercriminals from successfully logging in.
- Prevents Identity Theft and Phishing Attacks: By adding layers of verification, Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) make it harder for cybercriminals to steal personal information or conduct phishing attacks.
Common Authentication Methods
Security Tokens: Sucurity Tokens or Security Keys is a physical object like One-Time Password (OTP) or Time-Based One-Time Password (TOTP), that authenticate a user’s identity when tapped or inserted.
Biometric Authentication: Uses physical characteristics such as fingerprints, iris scans, or facial recognition. Biometric authentication is widely being used worldwide to improve online security.
Authenticator Apps: Applications like Google Authenticator, 1Password, or any other which is installed onto your smart phone that generates time-based one-time passwords (TOTPs) for online security within the App for seconds.
Key Summary
Cybersecurity has become critical and an important problem for every organization, even for cyber teams across the world. Implementing Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) options are key steps in securing digital identities, assets, and sensitive data. Many businesses and employees are sill not well aware about the importance of cybersecurity, that’ what pushing them behind. Learning and spreading awareness on network & cybersecurity topic is very essential for every individual and organization and it will also help in business continuity and disaster recovery planing. 立即聯繫我們, for free consultation now to secure your critical infrastructure and learn best strategies from our top-rated experts.