API認證中的 OAuth漏洞隱藏風險
The risks of OAuth vulnerability are becoming the go-to standard for API authentication and authorization, enabling third-party applications to access user data without exposing credentials. However, many developers mistakenly assume that implementing OAuth ensures foolproof security. In reality, the risks of OAuth vulnerability in API authentication can expose sensitive data, leading to account takeovers, unauthorized […]
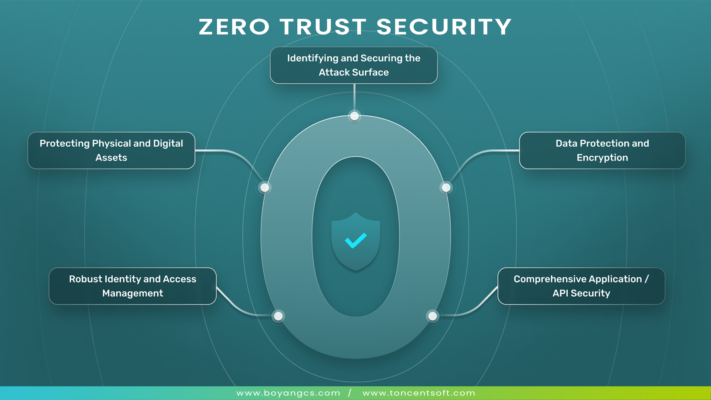
阅读全文What is Zero Trust Security?
The rapid growth of technological advancement is increasing on the other hand protecting data and networks is becoming more critical than ever. Traditional security models assume a trusted internal network and focus heavily on defending the perimeter. However, with more people working remotely and accessing resources from multiple devices, these models often fall short. Enter […]
阅读全文CVE-2024-0132 Vulnerability in NVIDIA Container Toolkit
As someone deeply immersed in cloud infrastructure security, we understand how a single vulnerability can expose an entire system to significant risk. Recently, a severe security flaw has been discovered in the NVIDIA Container Toolkit, tracked as CVE-2024-0132, that impacted 100K+ substantial risk to cloud environments using containerized workloads. If successfully exploited, this vulnerability could […]
阅读全文Network Security Threats and Vulnerabilities
Network security is a top priority for every business and individual due to the rapid adoption of advanced technologies where cybercrime is also increasing. On this stage, there are still 47% of businesses that don’t allocate any funds towards Network and cybersecurity. While, 51% of small businesses don’t utilize any IT security measures. 36% of small businesses […]
阅读全文How Fast Can AI Crack Passwords?
Humans use AI to detect malware and also cybercriminals use AI to detect passwords, sounds confusing right? Cyber threats are evolving at an alarming rate in Hong Kong and China, one of the most concerning developments is how quickly AI can detect passwords. If your password is weak or commonly used, it could be cracked […]
阅读全文Tips to Prevent Online Fraud
The world is digitalizing swiftly, and so are cybersecurity attacks. The rising demand for artificial intelligence, social media, and e-commerce platforms has made life more convenient but has also opened new back doors for cyber criminals. In Hong Kong SAR of China, a vibrant and booming economy embracing technological advancement, cybersecurity attacks are becoming increasingly […]
阅读全文Cybersecurity Myths: Facts Everyone Needs to Know
When it comes to cybersecurity, companies and individuals often operate based on misconceptions that can leave them vulnerable to cyber threats. These cybersecurity myths are prevalent, and many businesses mistakenly build their data security policies around them, or fail to review existing policies due to these misconceptions. As a result, they become easy targets for […]
阅读全文Data Security for Hong Kong Business
The data breach incidents continue to be a serious problem and threat to businesses and people in Hong Kong, so the data security is important for business growth to stay ahead of the cybersecurity attacks. In Hong Kong, data security for business is governed by the Privacy Commissioner for Personal Data (‘PCPD’) published a Guidance […]
阅读全文Security Risks of Cloud Computing
The security risks of cloud computing has been top problem worldwide. As cloud computing market in Hong Kong and China continues to a staggering $1,240.9 billion by 2027, understanding the security risks of cloud computing is essential for businesses. Although cloud computing environments may introduce certain cybersecurity threats, compared to traditional on-premises systems. While cloud […]
阅读全文