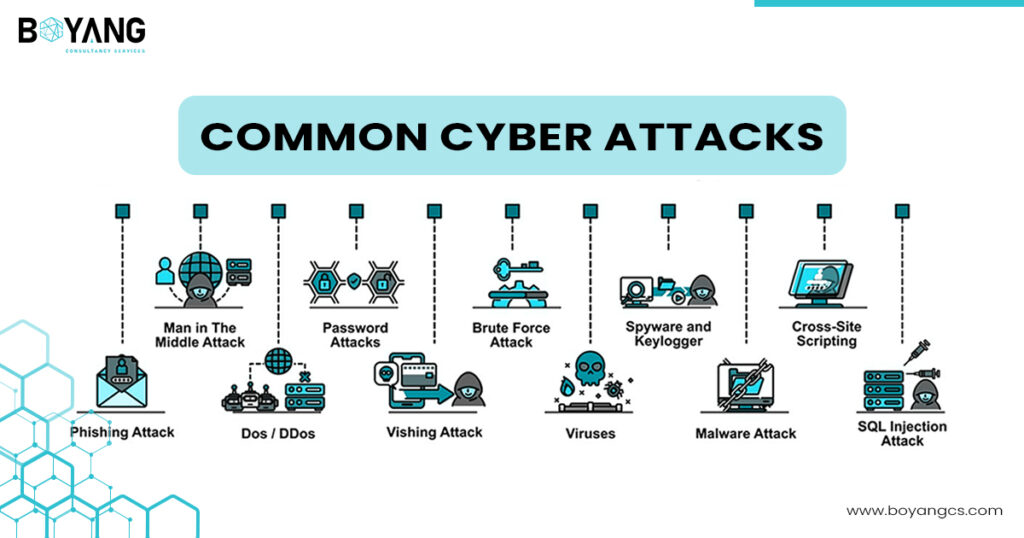
Cybercrime is a widespread problem for all businesses, but small businesses face a particularly severe risk. Cyber attacks can cause millions of damage to your systems and business, halt your operations, or even land you with fines due to data protection breaches. With 98% of cyber attacks on small businesses driven by financial methods, and small business employees receiving 350% more social engineering attacks than those of large enterprises, this threat is real.
Larger businesses and enterprises can more easily recover from big cyber attacks, whereas system damage, data loss, and fines but these can cripple smaller businesses. Only 16% of small businesses are very confident in their cyber security readiness, and many business owners aren’t familiar with the characteristics cyber criminals and importance of cyber security.
In this article, we have elaborated the most common types of cyber attacks faced by small businesses also learning about how to prevent your business from cyber attacks is very essential.
Social Engineering and Phishing
Social engineering is a type of cyber attack that manipulates authorized users into granting access to systems or revealing sensitive information. These attacks exploit human trust, tricking employees into believing that the attackers are credible sources. The most prevalent form of social engineering is phishing. Phishing emails are designed to deceive employees into handing over passwords, financial information, or other personal data. These emails often appear to be from trusted companies and services, requesting users to log in to address an issue with their account. Upon clicking these links, users are redirected to fake replicas of legitimate login portals. Once the employees enter their details, criminals can use this information for fraud or sell it on black markets.
Spear phishing is a more targeted approach, where attackers conduct research on a business and impersonate key individuals. These attacks are harder to detect as spoof emails can appear to come from colleagues or even managers. To prevent social engineering attacks, businesses should educate employees on identifying phishing attempts, implement multi-factor authentication (MFA), and use advanced email filtering systems.
Learn How to Stop Phishing Attacks? A complete guide to level-up your online security.
Malware Attack
Malware, short for malicious software, is a type of cyber attack where harmful software is being installed on a device without the user’s knowledge. The purpose of the malware attack is to steal the user data, damage system, or to gain unauthorized access. These attacks are typically executed through various methods like phishing emails, malicious downloads, or exploiting software vulnerabilities.
Once the cyber criminal installed the software on the user device, malware will perform malicious activities such as stealing sensitive information, encrypting data for ransom (ransomware), or creating backdoors for future attacks. Businesses must implement end-to-end cybersecurity measures, including regular software updates, employee training, and the use of antivirus programs, to protect against the ever-evolving threat of malware attacks.
Vishing Attack
Vishing is a type of cyber attack where criminals use voice messages and phone calls to deceive people into sharing personal information. The term “vishing” combines “voice” and “phishing,” and it primarily involves scam calls. With advanced phone technology like caller ID spoofing, vishing scams are becoming increasingly convincing. Scammers often pose as banks or credit card companies, claiming there’s an issue with your account or payment.
During the COVID-19 pandemic, as more employees work from home, vishing has become a significant problem for businesses. Cybercriminals can impersonate tech support or payroll departments remotely, making their scams more effective. Imagine the damage an attacker could cause if they tricked employees into revealing passwords or national insurance numbers. Protecting against vishing attacks requires awareness and strong security measures to keep personal and business information safe.
Smishing Attack
Smishing, or SMS phishing, is a type of cyber attack where criminals use text messages to deceive people into revealing personal information. In smishing attacks, you might receive messages like “You’ve missed a delivery you weren’t expecting,” “You’ve won a million-dollar prize, call this number or share your bank account details to claim it,” or “Your bank account is suspended, click this link to recover it.” These messages often contain links that lead to malicious websites designed to steal your information or infect your device with malware.
These cybercrime tactics can quickly put you in a dangerous situation, compromising your privacy and data security. The deceptive nature of smishing messages makes them particularly effective, as they often create a sense of urgency or excitement. To protect yourself, be cautious with unsolicited messages and never click on suspicious links or share personal information via text.
Whaling Attack
Whaling is a highly dangerous form of spear phishing where criminals impersonate senior executives like a CEO, CTO, company secretary, or general manager. In these attacks, cybercriminals exploit the authority and trust associated with these figures to trick employees into sharing sensitive information or authorizing fraudulent transactions.
In 2017, Uber fell victim to a whaling attack resulting in a data breach affecting millions of customers worldwide. The ride-share company allegedly paid hackers $100,000 to delete the stolen data and conceal the attack. Such incidents highlight the importance of verifying unusual requests, even when they appear to come from top executives, to protect your organization from these sophisticated cyber threats.
Angler Phishing
In angler phishing attacks, cyber criminal use social media or customer service accounts to entice victims into providing personal information and financial data. Criminals know that businesses are increasingly using social media channels to communicate with customers for a number of purposes, and are aware it provides a quick and easy method to receive personal information for fraud. Angler phishing also presents businesses with a huge problem for brand reputation. Successful social media spoofing attacks can hurt trust with your customers.
Denial of Service / DDoS Attacks
A denial-of-service (DoS) or distributed-denial-of-service (DDoS) attack is a cyber attack where criminals aim to crash a computer system or server, making websites and services unavailable to users. These attacks are often used by hacker groups to force websites offline by overloading web servers or sending data that causes the server to crash. This can be done through buffer overflow attacks, which consume server resources, or flood attacks, which saturate server capacity and use up bandwidth.
DDoS attacks, a more potent form of DoS attacks, utilize many distributed sources or botnet to overwhelm servers. This allows attackers to achieve the bandwidth needed to take down large websites. Such attacks can cause significant financial losses due to costly downtime, damage hardware, and harm a company’s reputation. Protecting against DoS and DDoS attacks is crucial to maintaining business continuity and customer trust.
Man in the Middle Attack
Man-in-the-middle (MitM) attacks occur when a third party intrudes into a two-way transaction and intercepts key data, often known as eavesdropping attacks. In these attacks, criminals can also manipulate conversations and transactions to retrieve sensitive information and orchestrate fraudulent exchanges.
MitM attacks remain undetected by leveraging the real-time nature of conversations and data transfers. Two common scenarios where MitM attacks are likely include:
- Unsecured public wireless networks: When employees use public Wi-Fi at places like coffee shops, or if offices don’t employ proper encryption, criminals can intercept internet traffic.
- Networks infected with malware: If a device or network has been compromised with malware, attackers can monitor and manipulate traffic.
To protect against MitM attacks, it’s crucial to use secure networks and ensure devices are free from malware.
SQL Injections
An SQL Injection attack involves inserting malicious code, known as statements, into a web server’s database. Structured Query Language (SQL) is the language used to manage databases, making it a popular target for web server attacks. In these attacks, criminals manipulate SQL databases to access unauthorized information. The hacking group “ResumeLoosters” has been actively selling the stolen information on Chinese-speaking hacking-themed Telegram groups since 2023. By injecting malicious SQL queries, the threat actors retrieved databases containing close to 2.2 million rows, with over 500,000 representing user data from employment websites.
Protecting against SQL injection attacks involves implementing SQL injection filtering to filter out invalid statements and using web application firewalls to detect and block malicious activities. Ensuring secure coding practices and regular security audits can further safeguard databases from these threats.
Drive-By-Downloads
A Drive-By-Download attack occurs when malicious software or viruses are downloaded onto your system without your consent. These attacks exploit flaws in applications or operating systems that allow unauthorized downloads of software patches. They can also occur when adware and malware are bundled with seemingly legitimate software downloads.
These downloads succeed by either tricking the user into unwittingly authorizing a download or bypassing authorization altogether. To protect against Drive-By-Download attacks, users should always be vigilant about what they download and install, ensuring software is from trusted sources and keeping their systems updated with the latest security patches.
Some Top News :
Conclusion
As businesses of all sizes increasingly adopt advanced technology, the incidence of cyber crimes continues to rise. Cyber criminals have developed a complex network of attacks and threats that can cause significant financial harm to small-to-large businesses.
Boyang’s network & cybersecurity experts are dedicated to protect your business from cyber security threats. Contact us today for a free security audit are dedicated to protecting your business from cyber security threats and a complimentary quote. We will identify vulnerabilities into your IT infrastructure and help you to address them.
Found this article interesting? Support us on LinkedIn, Twitter, WeChat and Facebook to read more compelling content.