A Chinese hacker group, commonly known as Mustang Panda, has been leveraging Visual Studio Code to carry out espionage attack against government entities in South East Asia. This innovative approach represents a growing trend in the use of legitimate software for malicious purposes.
Mustang Panda, also known by the other names such as BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, and Red Lich, has been operational since 2012, routinely conducting cyber espionage attacks by targeting government and religious entities across Europe and Asia, particularly those located in South China Sea countries.
Visual Studio Code for Espionage Attacks
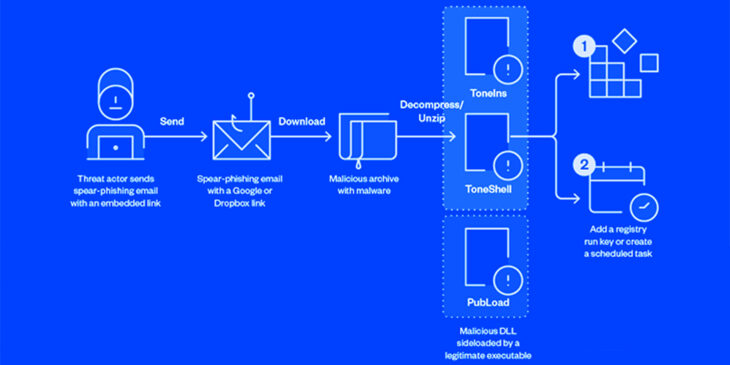
Researchers from Palo Alto Networks’ Unit 42 revealed that Mustang Panda has been utilizing Visual Studio Code’s reverse shell capabilities to gain unauthorized access to targeted networks. This technique, described as a “relatively new approach,” was first demonstrated in September 2023 and showcases how attackers are continuously evolving their strategies.
This hacker group appears to be a continuation of a previously documented attack targeting a Southeast Asian government entity. Mustang Panda has a history of conducting cyber espionage against government and religious organizations across Asia and Europe, with a particular focus on countries surrounding the South China Sea.
The Malicious Use of Visual Studio Code
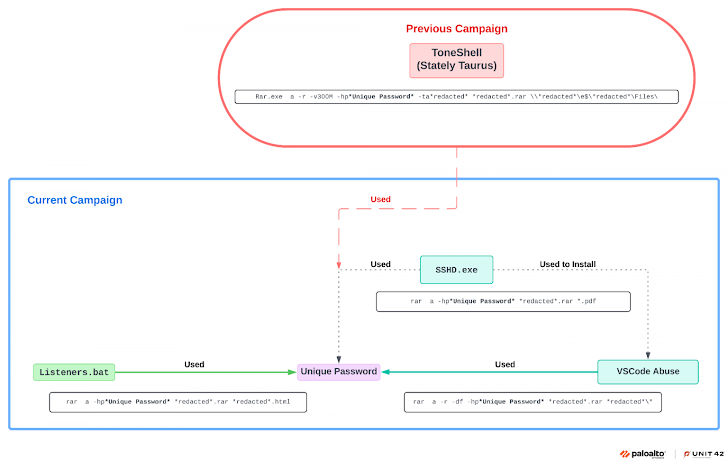
To exploit Visual Studio Code, attackers can either use a portable version of the software or gain access to an already installed version. By executing a specific command, attackers create a tunnel that links to a Visual Studio Code web environment. This access allows Mustang Panda to remotely run commands or create files on compromised machines.
Once inside, Mustang Panda has been observed using OpenSSH to execute further commands, transfer files, and move laterally across the network. The combination of Visual Studio Code and OpenSSH highlights the group’s ability to exploit commonly used tools in both development and network environments, making detection more difficult for traditional cybersecurity measures.
ShadowPad Malware & Potential Collaboration
Moreover, to the Visual Studio Code exploitation, researchers also uncovered activity linked to ShadowPad malware, a modular backdoor frequently employed by Chinese espionage groups. ShadowPad malware presence in the same environment as the Visual Studio Code-based attacks raises questions about whether two distinct threat actors were operating simultaneously or if Mustang Panda was collaborating with another Chinese hacker group.
While there is no definitive answer, the overlap between these activities underscores the complexity of modern cyber threats. The possibility of coordination between different actors further complicates the efforts to attribute attacks and defend against them.
The Broader Implications for Cybersecurity
This case highlights the growing trend of attackers using legitimate software tools for malicious purposes. As organizations increasingly rely on software like Visual Studio Code for development and operations, they must ensure that their cybersecurity measures can detect and mitigate these sophisticated threats.
Mustang Panda’s use of Visual Studio Code not only demonstrates their technical power but also serves as a reminder for government entities and businesses alike to remain vigilant and adopt comprehensive security strategies. This includes regular updates, rigorous security protocols, and proactive monitoring to safeguard against evolving cyber threats.
If you find this news article helpful, support us on LinkedIn、, Twitter、 和 Facebook,.