Odoo for Manufacturing Business in Hong Kong

Introducing Odoo Odoo is an open-source ERP, a suite of business management software that has 70+ integrated applications software. These Odoo apps are designed to simplify and streamline business operations. All Odoo ERP softwares are available in 30+ languages like Mandarin, Cantonese, English, etc. From CRM to Accounting, Manufacturing, Inventory, and Sales, Odoo provides everything […]
Why Odoo ERP is different from the traditional ERP?

When it comes to ERP (Enterprise Resource Planning) systems, manufacturing business got so many options. However, one ERP solution has been making waves. Odoo the best open-source ERP in Hong Kong, China and worldwide. Odoo software is gaining popularity for its modularity, cost-effectiveness, and user-friendliness, setting it apart from traditional ERP systems. Here’s a closer […]
What is Zero Trust Security?
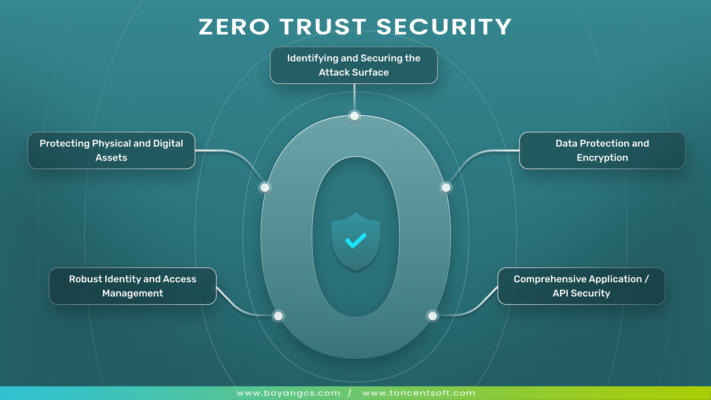
The rapid growth of technological advancement is increasing on the other hand protecting data and networks is becoming more critical than ever. Traditional security models assume a trusted internal network and focus heavily on defending the perimeter. However, with more people working remotely and accessing resources from multiple devices, these models often fall short. Enter […]
CVE-2024-0132 Vulnerability in NVIDIA Container Toolkit

As someone deeply immersed in cloud infrastructure security, we understand how a single vulnerability can expose an entire system to significant risk. Recently, a severe security flaw has been discovered in the NVIDIA Container Toolkit, tracked as CVE-2024-0132, that impacted 100K+ substantial risk to cloud environments using containerized workloads. If successfully exploited, this vulnerability could […]
Offshore Staff Augmentation: Key Transform Your IT Team

What is Offshore Staff Augmentation? In the Hong Kong IT market, business environment, organizations are constantly seeking ways to stay competitive, scale quickly, and reduce operational costs. Where many of Hong Kong companies are dealing with a shortage of skilled IT professionals and labor cost. Offshore tech staff augmentation is a quickly emerging as the […]
Network Security Threats and Vulnerabilities
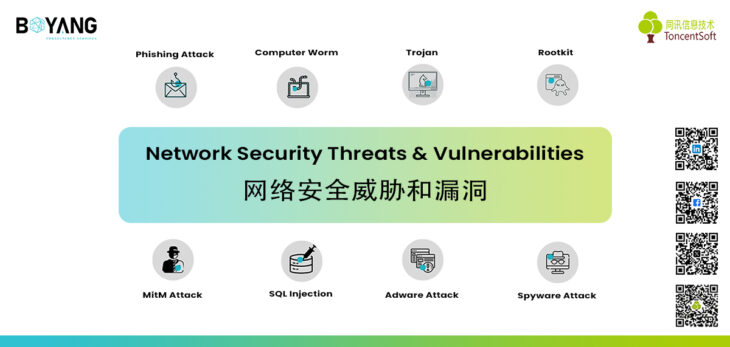
Network security is a top priority for every business and individual due to the rapid adoption of advanced technologies where cybercrime is also increasing. On this stage, there are still 47% of businesses that don’t allocate any funds towards Network and cybersecurity. While, 51% of small businesses don’t utilize any IT security measures. 36% of small businesses […]
Legacy System Migration: A Step-by-Step Guide

The tech world is modernizing faster, therefore, relying on legacy system can hinder your company growth and efficiency. Modernizing your legacy systems can enhance productivity, reduce costs, and transform your business. In order to implement digital transformation for your legacy system migration, self-scaling of your systems and application is very important. This article will provide […]
Recruiting Tech Talent in Vietnam

The 74% of Hong Kong companies are facing high labor cost and tech talent shortage. In these circumstances, recruiting tech talent in Vietnam has become the best tech talent option for IT companies seeking skilled IT professionals at while reducing labor cost rates and to beat tech talent hiring mistakes. With a fast growing tech […]
Tips to Reduce Labor Costs: For Hong Kong Companies

Recruiting the best tech talent in Hong Kong is always a significant challenge for many large IT companies and IT recruiters due to rising labor costs and a shortage of tech skills. Due to the fastest growing technical advancement, all the companies want to stay ahead of the curve by finding cost-effective solutions for recruiting […]
Subcontracting for Tech Talent

Many tech companies in Hong Kong are shifting their tech recruitment strategies towards subcontracting to access global tech talent without compromising on lack of local skilled professionals. With the talent shortage gap increasing in Hong Kong, subcontracting for tech talent is becoming an essential strategy for businesses to remain competitive and to avoid buzzing IT […]
