Tips to Prevent Online Fraud

The world is digitalizing swiftly, and so are cybersecurity attacks. The rising demand for artificial intelligence, social media, and e-commerce platforms has made life more convenient but has also opened new back doors for cyber criminals. In Hong Kong SAR of China, a vibrant and booming economy embracing technological advancement, cybersecurity attacks are becoming increasingly […]
Cybersecurity Myths: Facts Everyone Needs to Know

When it comes to cybersecurity, companies and individuals often operate based on misconceptions that can leave them vulnerable to cyber threats. These cybersecurity myths are prevalent, and many businesses mistakenly build their data security policies around them, or fail to review existing policies due to these misconceptions. As a result, they become easy targets for […]
Data Security for Hong Kong Business

The data breach incidents continue to be a serious problem and threat to businesses and people in Hong Kong, so the data security is important for business growth to stay ahead of the cybersecurity attacks. In Hong Kong, data security for business is governed by the Privacy Commissioner for Personal Data (‘PCPD’) published a Guidance […]
Technical Skills Shortage in Hong Kong

The Hong Kong is famous for its strong economy, lifestyle and technological advancement in the global financial hub. In the sense of present, the Hong Kong is juggling with a technical skills shortage. This technical skills shortage in Hong Kong has been increasing by a notable net outflow of tech talent in recent years. In […]
Security Risks of Cloud Computing

The security risks of cloud computing has been top problem worldwide. As cloud computing market in Hong Kong and China continues to a staggering $1,240.9 billion by 2027, understanding the security risks of cloud computing is essential for businesses. Although cloud computing environments may introduce certain cybersecurity threats, compared to traditional on-premises systems. While cloud […]
Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA)
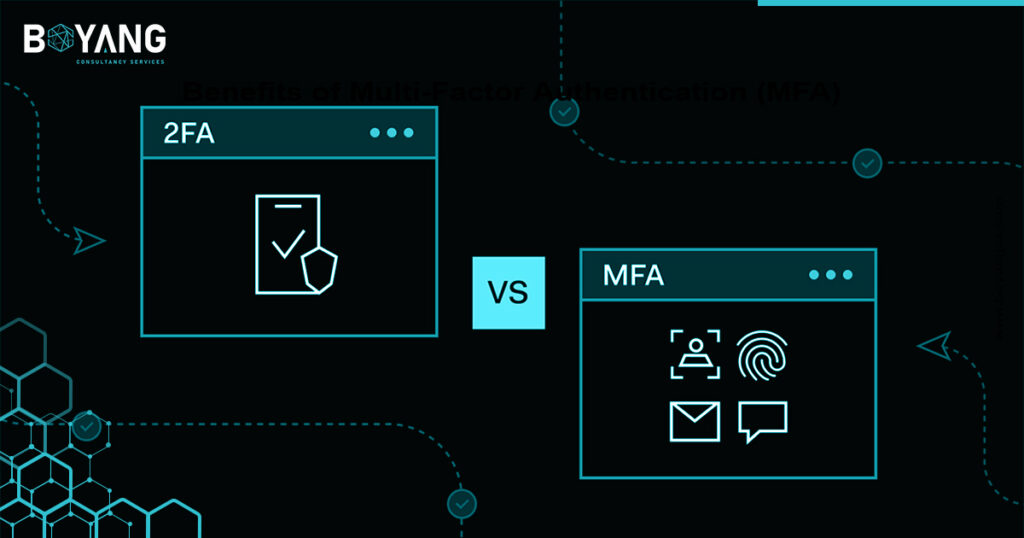
The online security of digital accounts and sensitive information has become more critical than ever. Cybercriminals have become increasingly adept at breaching systems and stealing data. They can crack 90% of passwords easily within an hour. That’s why making advanced authentication methods is very essential for businesses and individuals. Two-Factor Authentication (2FA) and Multi-Factor Authentication […]
Managing Tech Recruitment Risks in China

To manage tech recruitment in China carries inherent risks. Non-compliance with labor laws and violations of employment equality and personal information protection regulations during the recruitment process can result in administrative penalties or other legal consequences. Understanding the relevant risk points and compliance issues is crucial for businesses operating in China. Managing Tech Recruitment Risks […]
How to Stop Phishing Attacks: A Complete Guide

How to stop phishing attacks? A a big question and problem for every organization and security teams everywhere in the world. It can also inflict long-term damage to an organization’s reputation. Cybercriminals use email, SMS, and voice calls to trick people and steal their sensitive information. The shift to remote work during the COVID-19 pandemic […]
Common Types of Cyber Attacks
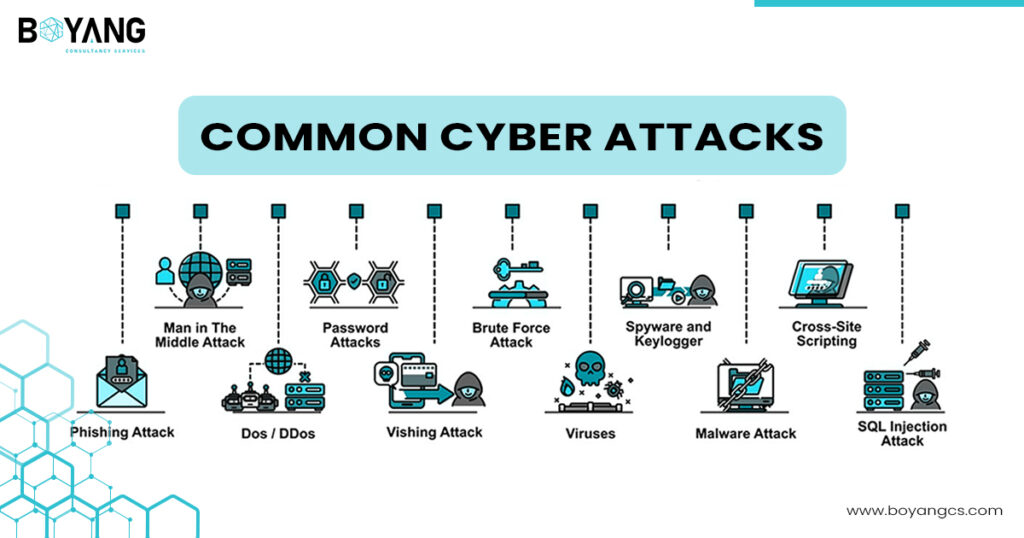
Cybercrime is a widespread problem for all businesses, but small businesses face a particularly severe risk. Cyber attacks can cause millions of damage to your systems and business, halt your operations, or even land you with fines due to data protection breaches. With 98% of cyber attacks on small businesses driven by financial methods, and […]
Technical Hiring in Hong Kong: Guide 2024

The job market in Hong Kong faced significant challenges in 2023, impacted by global recession concerns, higher interest rates, economic headwinds in China, and a domestic economic slowdown. Companies adopted conservative approaches, focusing on cost control with longer interview processes and more layers of approvals before extending offers to potential candidates. Professionals, in turn, prioritized […]
