One of the most alarming trend in recent years is the session hijacking, an attack method that allows hackers to bypass authentication mechanisms, including MFA, and take control of user sessions in cloud-based apps and services.
This new form of session hijacking 2.0 is far more sophisticated, with attackers now targeting identity-based attacks over the public internet, instead of relying on the old network-based attacks like Man-in-the-Middle (MitM). As reported by Microsoft, in 2023 alone, there were 147,000 token replay attacks, a 111% increase compared to the previous year, highlighting the rapid rise of these new attacks. Google has detected session cookie attacks now happen at the same frequency as traditional password-based attacks.
But how did session hijacking evolve, and why is it posing such a challenge for businesses relying on cloud security?
What is Session Hijacking 2.0?
The session hijacking involved in MitM attacks, where attackers intercepted unsecured local network traffic to capture credentials or session IDs. These early attacks typically targeted sensitive information like credit card details, leveraging client-side attacks such as Cross-Site Scripting (XSS) to steal session IDs from compromised websites.
However now a days, session hijacking has taken a different approach. Modern session hijacking is more about identity theft and token stealing in cloud environments. Attackers no longer need to intercept local network traffic; instead, they focus on cloud-based services where they can steal valid session cookies or tokens from a user’s browser, resuming the session on their own devices. These attacks are not just limited to stealing login credentials but can bypass security layers such as MFA, encrypted traffic, and VPNs, which were once reliable defenses.
Why are Session Hijacking Attacks Dangerous?
Session hijacking allows attackers to take over an active session without needing the user’s login credentials or bypassing MFA entirely. Once a hacker has gained control over the session cookie or token, they can impersonate the victim, accessing sensitive apps and data as if they were the legitimate user.
Why is session hijacking best for cybercriminals? The reason include:
- Bypassing MFA: Modern phishing attacks or infostealers allow attackers to grab the session tokens of authenticated users, bypassing MFA entirely. These tokens can remain valid for days or even months in some cases.
- Identity-as-the-Perimeter: With most organizations relying on Single Sign-On (SSO) solutions like Okta, an attacker who compromises one session can gain access to a whole suite of apps without further authentication.
- Cloud App Vulnerabilities: With users managing multiple accounts across various cloud apps, attackers can target these sprawling environments to extract valuable customer data, intellectual property, or other sensitive information.
The New Tactics of AitM, BitM, and Infostealers
Latest session hijacking attacks rely heavily on advanced phishing toolkits and malware like infostealers. Here’s how these methods work:
1. Advanced Phishing Kits (AitM and BitM):
- AitM (Attacker-in-the-Middle) toolkits allow the hacker to act as a proxy between the user and the authentication service. In this process, the victim unknowingly completes the MFA step, while the attacker captures the session tokens and uses them to hijack the session.
- BitM (Browser-in-the-Middle) is even more deceptive. This method tricks the victim into controlling the attacker’s browser remotely. Essentially, the attacker gives the victim access to their browser, and once the victim logs in, the attacker resumes control, armed with the victim’s authenticated session.
2. Infostealers:
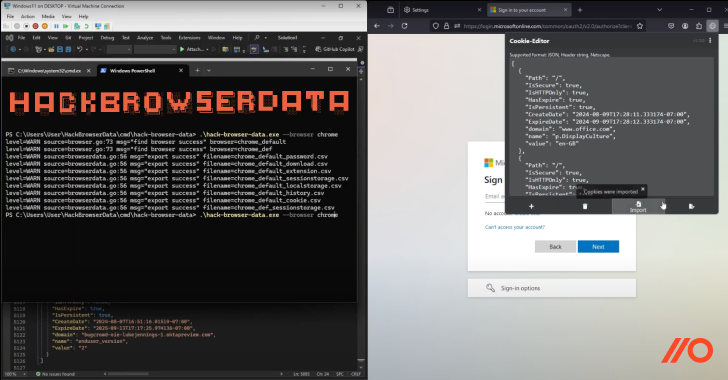
- Infostealers are widely used to harvest session cookies from browsers, especially targeting those synced across multiple devices. These attacks are more opportunistic compared to AitM, infecting victims through malicious ads, P2P downloads, social media links, or compromised websites. Once the infostealer has accessed the session data, it can be used to log in to sensitive apps without any reauthentication.
- Infostealers are particularly dangerous in BYOD (Bring Your Own Device) environments, where employees may sync personal and corporate data across multiple devices. A personal device infected with an infostealer can lead to corporate credentials being compromised, as browser profiles often sync across devices.
Why Infostealers are Hard to Detect?
Many organizations rely on Endpoint Detection and Response (EDR) systems to identify and block malicious activity. However, infostealers often evade detection, especially when sophisticated attackers use custom malware. The problem becomes more pronounced in BYOD settings or when contractors use unmanaged devices. Additionally, infostealers often target personal devices that aren’t as rigorously protected, which can then sync corporate data to infected devices.
Even EDR solutions with top-tier defenses aren’t foolproof against these evolving threats, leaving many organizations vulnerable to session hijacking.
Passkeys in Session Hijacking
Passkeys, designed to be phishing-resistant, are effective in preventing AitM and BitM attacks, as they eliminate the need for users to complete authentication steps. However, they are less effective against infostealers, as these attacks focus on session tokens rather than the login process. Once the session is active, the attacker can bypass the need for re-authentication entirely.
How to Detect and Respond to Session Hijacking
Detecting session hijacking is challenging, but several layers of defense can be applied:
- Preventing Malware Delivery: Implement robust controls to block malicious ads, infected websites, and malvertising before they reach end-users. However, this alone won’t stop all attacks.
- Monitoring for Unauthorized Sessions: Once an attacker has stolen a session cookie, app-level controls like IP restrictions or geolocation filters may help detect unauthorized access attempts. However, these controls can be bypassed with proxy networks or residential proxies.
- Browser-Based Detection: One innovative approach introduced by Push Security is injecting a unique marker into a browser’s user agent string. When the session token is stolen and used on another device, security teams can detect the change by checking for a mismatch in the marker—effectively alerting them to session hijacking attempts.
“Check out this video demo to see how session hijacking works in real time.”
Conclusion
The rise of session hijacking signals a new era in identity-based cyberattacks. With the majority of companies relying on cloud services and SSO solutions, protecting sessions has never been more critical. As the data shows, traditional security mechanisms like MFA, VPNs, and EDR solutions are no longer sufficient on their own. By implementing behavior-based monitoring model, organizations can add a strong layer of defense to their network & cybersecurity. Contact us for a FREE security audit & expert solutions.
Found this article interesting? Support us on LinkedIn, Twitter and Facebook to read more compelling content.