The risks of OAuth vulnerability are becoming the go-to standard for API authentication and authorization, enabling third-party applications to access user data without exposing credentials. However, many developers mistakenly assume that implementing OAuth ensures foolproof security. In reality, the risks of OAuth vulnerability in API authentication can expose sensitive data, leading to account takeovers, unauthorized access, and critical security breaches.
Understanding these hidden risks is crucial for ensuring secure OAuth implementation. In this article, we will explore common OAuth vulnerabilities in API authentication, and discuss how to mitigate them effectively.
What is OAuth Vulnerability?
OAuth (Open Authorization) vulnerability is a security weakness in the OAuth authentication and authorization process that attackers can exploit to gain unauthorized access to third-party applications without needing user credentials. A common OAuth security risk arises from misconfigurations that allow attackers to steal authorization codes or access tokens, enabling them to impersonate users and access sensitive data.
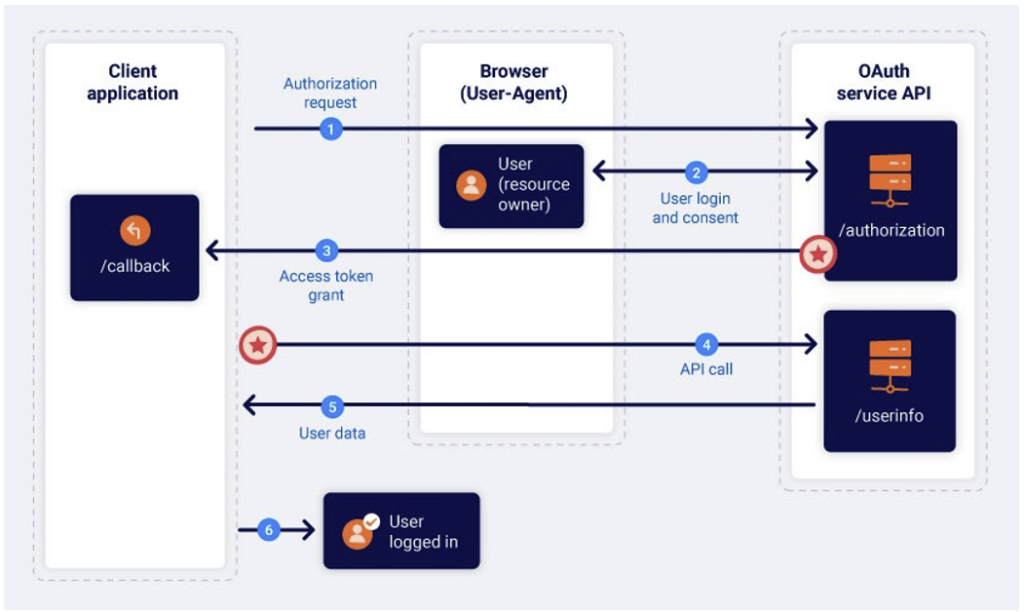
While OAuth enhances security by allowing users to grant app permissions without sharing passwords, improper implementation can lead to serious vulnerabilities, making it crucial for developers to follow best practices to prevent OAuth-based attacks.
Read this blog to understand: How 2FA and MFA Works?
Common Risks of OAuth Vulnerability
OAuth vulnerabilities typically arise due to misconfigurations, poor implementation, or security flaws in the authorization flow. Below are some of the most common risks associated with OAuth authentication:
1. Cross-Site Request Forgery (CSRF): CSRF attacks manipulate an authenticated user’s session to perform unintended actions. If OAuth lacks adequate CSRF protection, attackers can trick users into authorizing malicious requests.
How to Fix Cross-Site Request Forgery: Implement state parameters to verify legitimate authentication requests.
2. Redirect Attacks: Malicious actors can manipulate the redirect URI to steal authentication tokens or session credentials.
How to Fix Redirect Attacks: Always validate redirect URIs and enforce strict allow lists.
3. Mutable Claims Attack: Attackers can modify token claims (e.g., user roles or privileges) if signature validation is weak or absent.
How to Fix Mutable Claims Attack: Use signed tokens with strong cryptographic algorithms (e.g., JWT with HMAC or RSA signatures).
4. Client Confusion Attack: When multiple OAuth clients use the same credentials, an attacker can hijack sessions by redirecting users to an unauthorized client.
How to Fix Client Confusion Attack: Assign unique credentials to each client and validate client identities before granting tokens.
5. Scope Upgrade Attack: Malicious applications can request broader access scopes than initially intended, escalating privileges for unauthorized operations.
How to Fix Scope Upgrade Attack: Implement strict scope validation and obtain user consent before expanding access.
6. Redirect Scheme Hijacking: Mobile apps using deep linking can be exploited by attackers who register fraudulent schemes to intercept OAuth tokens.
How to Fix Redirect Scheme Hijacking: Use HTTPS-based redirects and enforce secure URL schemes.
How to Secure OAuth API Authentication?
To mitigate the risks of OAuth vulnerability, developers should follow best practices of OAuth to secure APIs. These current practices include:
- Always use Authorization Code Flow with PKCE for better security.
- Store access tokens securely (avoid client-side storage like localStorage).
- Implement short-lived tokens with automatic refresh mechanisms.
- Use HTTPS to prevent token interception.
- Enforce strict redirect URI validation to block token redirection attacks.
- Monitor OAuth logs and detect suspicious activity.
- Educate users about phishing risks and trusted application approvals.
Wrap-up
OAuth is a powerful authentication standard, but it is not immune to security threats. The risks of OAuth vulnerability in API authentication can lead to severe data breaches if not addressed properly. By implementing security best practices, organizations can safeguard their APIs against OAuth-related threats and ensure robust access control. Need expert guidance on securing your OAuth implementation? Contact our IT security team today for free consultation and audit report.
Found this article interesting? Support us on LinkedIn, Twitter, WeChat and Facebook to read more compelling content.






